The Windows Task Scheduler is abused by malware to hide itself. This hacking tool called Tarrask uses a previously unknown bug to remove the Security Descriptor registry. As a result, the malicious process is not noticed by the scheduler. This preserves access to hacked devices even after a reboot.
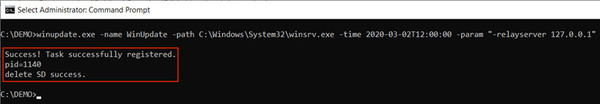
Microsoft writes that in a blog post to create awareness around the attacks. These come from Hafnium, a Chinese government sponsored group that was part of the Microsoft Exchange Meltdonw. The enormous amount of data released in the process would be used by China for ai development. The Tarrask software is used to keep malware-infected systems vulnerable without being noticed. For this, the entire process could also be deleted but then access would be lost after a restart.
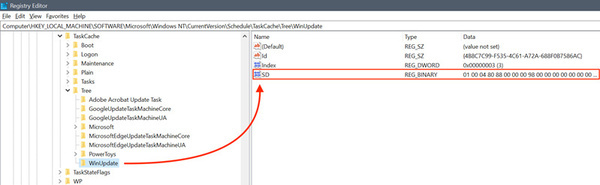
The hidden tasks can only be found manually by searching the Windows Registry for tasks without a security descriptor value in the Task Key. In the logs of Security.evtx and Microsoft-Windows-TaskScheduler/Operational.evtx, the hiding of these tasks may also be noticed. The manufacturer recommends that connections with sensitive data be closely monitored. Furthermore, no definitive solution to the bug is yet offered.
source: Hardware.info





