Millions of routers from Linksys and Netgear and other IoT products are affected by an unresolved dns vulnerability. Security researchers at Nozomi Networks Labs discovered CVE-2022-05-02, a bug in the dns implementation in two popular C libraries. uClibc and uClibc-ng are mainly used in routers and IoT products.

The administrator says that he has not been able to develop a solution himself. Therefore, with a 30-day waiting period, the security hole was finally published, in the hope that someone else would manage to implement a fix. In addition to Netgear and Linksys, Axis Communications also uses the uClibc library, as does the Linux distribution Embedded Gentoo. uClibc-ng is a fork designed specifically for the router OS OpenWRT.
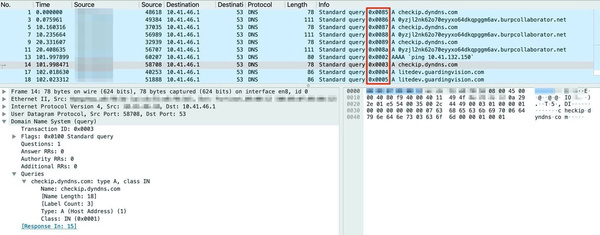
The transaction ids in the red outline are predictable.
The vulnerability is caused by the predictability of transaction identifiers. These are generated when processing dns requests. Attackers can perform so-called dns poisoning by finding out the transaction ids. When a user enters a web address an incorrect ip address is then returned.
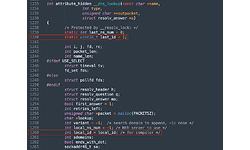
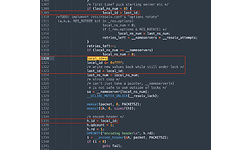
The value last_id can be predicted and filled in by the attacker.
This allows victims to be redirected to malicious websites without noticing. The attacker could steal or manipulate information and perform further attacks on the device. The biggest problem is that it is hard to tell whether the correct or a poisoned ip address is being returned.
Due to the severity of the vulnerability and the lack of a fix, no details have been disclosed about the affected devices.
Source: Hardware.info





